Why sensitive data still leaks
out
"Details of nearly 100 cases of data breaches, two thirds committed by government departments or other public sector bodies have been passed to the authorities", said Richard Thomas the UK Information Commissioner.
As of 2010, UK Government departments and corporate industry are still failing to apply adequate standards for data security. Organisations that have lost significant amounts of "sensitive" computer data include the NHS, the MOD,
the police, HMRC, and the security services.
How can this be, surely there are systems in place to prevent this from happening. Well, there are systems in place but sometimes they fail. All too often embedded
control measures include reliance on procedure and/or make incorrect assumptions about human behaviour.
Rules and legislation only work on persons that are law abiding, so it's no good just asking people to follow procedure. Even when there is no real intent to cause
a breach or harm, rules easily get broken through ignorance,
|
 |
laziness or a simple lack of awareness of what the bad guys can do with, or without,
technology. Chelsfield consultants have been tactically and strategically involved in
the design and implementation of security systems long before
personal computers or network structures were in common use.
Essentially the problems associated with maintaining data integrity, or any other kind of security for that matter, haven't changed. It's just that nowadays there's much more complexity around and subsequently a corresponding increase in the opportunity for things to go pear shaped.
The staff of many organisations are mostly unaware of how sensitive data can leak out, or what's needed to prevent it. We can assist with basic instruction for you, or your staff, and can arrange to hold one-day in-house seminars with a variety of organisations participating in the training.
If you ask us to arrange or participate in a
seminar, we won't use the opportunity to try and
sell things to you.
Wherever possible, Chelsfield data security systems work in the background, this overcomes the problem of having to rely on individuals working with cumbersome procedures. We have developed proprietary data encryption modules and authentication code systems that can be applied in a wide variety of ways. For example, as part of a third party program. To find out how this might benefit you, please contact us today at the address below.
|
|

|
|
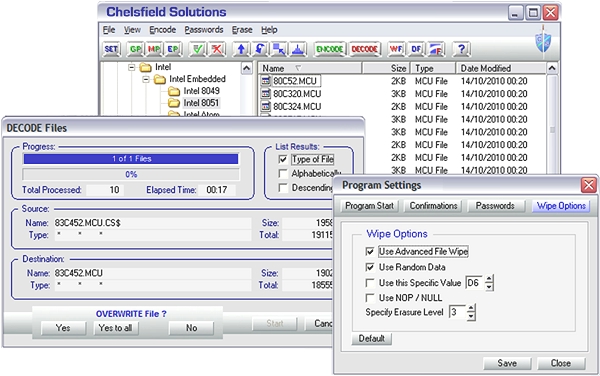
Self-Contained
Lock-Down using Chelsfield Encryption Wrapper
|
Typical
Chelsfield custom-written security
program to meet specific needs. The
underlying encryption method AES, RC4, Blowfish etc., remains transparent. The
inbuilt file-wipe exceeds requirements
of US Defense Std. 5220,22-M |
|

|
Chelsfield
Encryption Systems
Chelsfield can
assist you specify, then write and supply custom
encryption systems to suit your needs. These can be based on strong block ciphers such as AES,
RC4, Blowfish, 3DES,
or Twofish.
Alternatively,
we have also
supplied customised, as well as many third party, programs based on a proprietary
Chelsfield polymorphic stream
cipher. Polymorphic refers to a "rotating barrel" algorithm
to generate PRNG seeds and to ensure hash collision
resistance. We usually wrap this fast algorithm inside a Dynamic Link Library (.DLL )
file that has a small foot print and provides simple real time access.
The technique is platform independent and the code may be used to encrypt any binary data stream.
Itís also fast enough to be used "on-the-fly" in many applications.
Programs can be supplied with biometric access
coupled to more conventional authentication techniques to
provide very strong perimeter control barriers. Passwords may be
held in encrypted form in memory for the current session
but are retired automatically under user pre-set
rules that can only be modified, not defeated.
Passwords are never written out to disc or other
storage.
For Microsoft operating systems, the software can be packaged as an in-process server.
An advantage to this is that additional custom routines can be written which
may be deployed
as part of a single library (.DLL) file, or run as a background service on Windows 2000/XP/Vista/Win7 platforms.
|
|

|
|
Passwords:
a very weak link
No
matter how effective the data security system is, it
invariably hangs on the strength of a user password.
It is surprising how many people think they have a
secure password by adding a few numbers to a date or
a name. The idea that "no one will guess
it" may even be true! However, this does
not make for a strong password. As an example take
the password: [ 128April1966 ]. A brute-force or
dictionary attack will compose this string in a
matter of milliseconds. It is a very weak password.
Passwords
should be formed from as random a character string as possible,
including alpha numeric's together with symbols. There
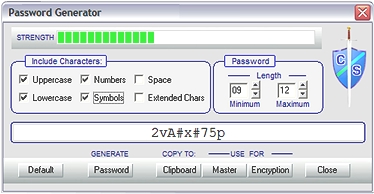
are, readily available, small utility programs designed to
generate random password strings as seen here to the
right. This Chelsfield example will enable you to set the minimum and
maximum password length and set what types of character are
to be included. The utility also indicates what strength,
measured by conventional metrics, the password is considered
to be.
|
 |
|
|
|
Chelsfield
Password Generator V1.02 |
|
|
|

